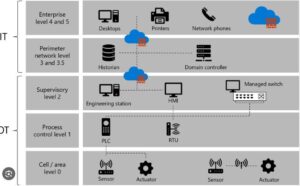
In the realm of Industrial Control Systems (ICS) security, the Purdue Model, also known as the Purdue Reference Model, has emerged as a prominent framework for establishing a secure and efficient architecture. Initially developed in the 1990s, the Purdue Model provides a reference for data flows in Computer-Integrated Manufacturing (CIM), where computer systems control and automate the entire production process.
Understanding the Purdue Model
The Purdue Model forms an integral part of the Purdue Enterprise Reference Architecture (PERA). It serves as a blueprint for organizing and segmenting ICS networks into distinct zones, ensuring a hierarchical flow of data between the different layers. By implementing the Purdue Model correctly, organizations can establish an “air gap” between their Operational Technology (OT) systems and Information Technology (IT) systems, thereby enhancing security and enabling effective access controls without impeding business operations.
The Purdue Model divides the ICS architecture into six zones, accommodating both IT and OT systems. Each zone plays a crucial role in the overall functioning and security of the ICS network. Let’s explore each of these zones in detail:
1. Level 4/5: Enterprise Zone
The topmost zone in the Purdue Model is the Enterprise Zone. This zone encompasses the typical IT network where primary business functions occur, such as manufacturing operations orchestration. Enterprise Resource Planning (ERP) systems, which drive plant production schedules, material utilization, shipping, and inventory management, are housed in this zone. Disruptions in this zone can have severe consequences, including prolonged downtime, economic damage, critical infrastructure failure, and revenue loss.
2. Level 3.5: Demilitarized Zone (DMZ)
Sitting between the IT and OT zones, the Demilitarized Zone (DMZ) serves as a buffer or convergence layer. It comprises security systems like firewalls and proxies, which prevent lateral threat movement between IT and OT environments. As automation and bidirectional data flows between OT and IT systems increase, the DMZ facilitates seamless integration while also posing potential cyber risks if a flat network approach is adopted.
3. Level 3: Manufacturing Operations Systems Zone
The Manufacturing Operations Systems Zone is where customized OT devices reside, managing production workflows on the shop floor. This zone includes various components:
- Manufacturing Operations Management (MOM) systems, which oversee production operations.
- Manufacturing Execution Systems (MES), which collect real-time data to optimize production.
- Data historians, which store process data and perform contextual analysis in modern solutions.
Disruptions in this zone can lead to economic damage, critical infrastructure failure, risks to personnel and plant safety, and revenue loss.
4. Level 2: Control Systems Zone
The Control Systems Zone encompasses systems responsible for supervising, monitoring, and controlling physical processes within the ICS network. Key components in this zone include:
- Supervisory Control and Data Acquisition (SCADA) software, which oversees and controls physical processes, locally or remotely, and aggregates data for historians.
- Distributed Control Systems (DCS), which perform SCADA functions and are typically deployed locally.
- Human-Machine Interfaces (HMIs), connecting to DCS and Programmable Logic Controllers (PLCs) to enable basic controls and monitoring.
5. Level 1: Intelligent Devices Zone
The Intelligent Devices Zone consists of instruments that send commands to devices at Level 0. Key components in this zone include:
- Programmable Logic Controllers (PLCs), responsible for monitoring automated or human inputs in industrial processes and making corresponding output adjustments.
- Remote Terminal Units (RTUs), connecting hardware in Level 0 to systems in Level 2.
6. Level 0: Physical Process Zone
At the lowest level of the Purdue Model, the Physical Process Zone comprises sensors, actuators, and other machinery directly involved in assembly, lubrication, and other physical processes. Modern sensors in this zone communicate directly with monitoring software in the cloud through cellular networks.
Relevance of the Purdue Model in Modern ICS Networks
With the emergence of the Industrial Internet of Things (IIoT), there has been speculation about the continued relevance of the Purdue Model in securing modern ICS networks. While the traditional hierarchical structure of the Purdue Model may not align perfectly with the evolving technology landscape, it still serves as a valuable starting point for securing OT networks.
One of the advantages of the Purdue Model is its clear hierarchy and well-defined system components. The distinct layers and logical boundaries within the model facilitate network segmentation, enabling effective access control and security measures. Even though IIoT devices may introduce new complexities to the ICS architecture, the Purdue Model’s hierarchical topology can still be adapted to enhance network security.
Challenges in ICS Security
Securing ICS networks presents unique challenges that demand tailored solutions. Here are some of the key challenges faced in the realm of ICS security:
1. The Ineffectiveness of the Air Gap
The traditional air gap approach, which physically isolates OT systems from external networks, is no longer sufficient in today’s interconnected world. The rise of IoT and cloud adoption has integrated industrial networks to such an extent that an isolated air gap is no longer effective in preventing cyber threats.
2. Legacy Devices
Many ICS devices were designed with a focus on longevity and reliability, rather than adaptability and security. These legacy devices often lack essential security features and are challenging to update or replace due to stringent uptime requirements. Consequently, these devices remain vulnerable to modern attacks while still being connected to the wider network.
3. IT-OT Convergence
The convergence of IT and OT environments introduces new security risks. As digital transformation breaks down the barriers between these domains, advancements in networking and data analytics reshape processes. However, ICS frameworks are often slow to adapt to these changes, leaving networks vulnerable to evolving cyber threats.
4. Hesitation to Adopt Zero Trust
Many ICS network owners are hesitant to embrace the zero trust security model. Concerns regarding potential downtime, revenue loss, infrastructure disruption, and safety risks make industrial operators cautious about the trade-offs in terms of cost and complexity. However, zero trust remains the most effective strategy for securing modern networks.
The Role of Zero Trust in ICS Security
The need for a comprehensive and resilient security approach in ICS environments has led to the adoption of the zero trust model. Zero trust security aims to establish a trust-nothing, verify-everything approach, both within and outside the network perimeter. It prioritizes the verification of all entities attempting to access systems and resources, regardless of their location or previous trust status.
Implementing zero trust principles in ICS environments can simplify security and address key challenges. It involves implementing microsegmentation at the network level, ensuring that access controls are applied based on device attributes, risks, and OT protocols. By monitoring east-west communication, organizations can detect anomalies and apply granular security rules to control traffic across zones.
One significant advantage of zero trust in ICS environments is the ability to provide secure remote access to ICS assets without the need for physical segmentation at each layer. This allows for secure maintenance and troubleshooting of ICS systems while minimizing disruption to operations.
Additionally, zero trust can help address the security risks associated with wireless connectivity in ICS networks. As private cellular networks gain traction, enabling mobility and standardized technology, zero trust principles can be applied to ensure secure and reliable remote access to Industrial Internet of Things (IIoT) and OT devices.
Conclusion
The Purdue Model continues to hold relevance in securing ICS networks despite the evolving technology landscape. Its hierarchical structure and logical boundaries provide a solid foundation for network segmentation and access control. However, as IIoT devices and digital transformation reshape ICS architectures, organizations must adapt the Purdue Model to address new complexities and challenges.
CTA: To learn more about Cybersecurity best practices and how to protect your critical infrastructure, Contact us today:1(647)948-6768,info@securitdata.ca